Computer security
CIFOR Working Paper: Assessing current social vulnerability to climate change: A participatory methodology
This paper describes a participatory methodology used to assess the current vulnerability of local communities in the Congo Basinon the COBAM project. Vulnerability has been studied through the lenses of different dimensions: system and exposure units, dynamic processes, multiple threats, differential exposure, social capital and collective action. The purpose of this framework is to grasp the socio-ecological dynamics in the system over the past decades, in order to identify future actions for reducing vulnerability and to enhance adaptive capacity.
Issues around developing and working with vulnerability indicators at the urban level in Europe
Vulnerability indicators are a valuable tool to identify vulnerable spots, guide the allocation of adaptation funding, communicate and raise awareness, and monitor the effectiveness of policies.
Guidance for Assessing Vulnerability
Guidance for assessing vulnerability and links to examples
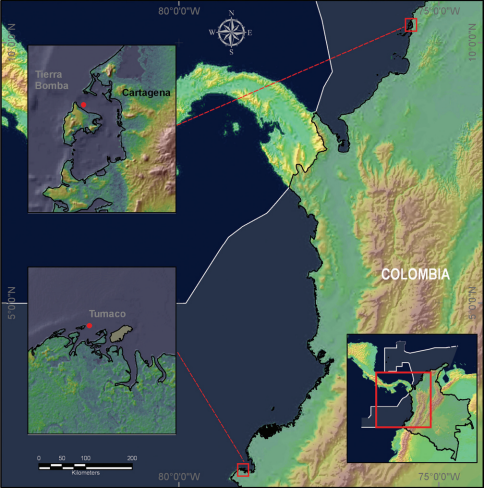
Methodology of Colombia NCAP Project
This article describes the methodological framework used in the Colombia NCAP project.